Why Security Is Now the First Gate to B2B Commerce
It usually doesn’t collapse in the sales meeting. The numbers make sense. The buyer is nodding. Procurement likes the terms. Everything feels lined up. And then someone higher up in the chain says five words that freeze the room:
“We’ll need CISO approval first.”
That’s where so many industrial e-commerce deals stall. The Chief Information Security Officer isn’t looking at your catalog, your pricing, or your delivery timelines. They’re looking at your buyer portal. They want to know: does it protect their data, their networks, and their plant floor from risk?
And the truth is, most supplier portals don’t. They’re built to move orders, not to withstand a security audit. Outdated apps sit unpatched. CAD file libraries are exposed without proper access controls. Order histories are stored in ways that can be scraped or stolen. To a sales team, these things seem invisible. To a CISO, they’re red flags.
That’s why deals that feel “won” in the front office can still die in the back. A contract worth millions can vanish overnight because the portal didn’t pass a security test. In industrial manufacturing, where OT and IT are tied closely together, cyber-risk isn’t a theoretical line item. It’s an operational threat. And the executives buying from you won’t take that chance.
This guide is built for the suppliers who have felt that pain or who know it’s coming. It’s not about generic compliance. It’s about passing the only test that matters once the CISO takes a hard look: can your portal hold up under scrutiny?
The C-Level Reality: Why Cyber Risk Kills Deals Before They Start
Executives don’t lose sleep over whether your portal looks clean or your checkout flow is smooth. They lose sleep over headlines, a ransomware attack that shut down a supplier, a phishing breach that leaked order history, or a cyber-attack that jumped from a vendor’s system into a plant-floor network.
In industrial manufacturing, the stakes are higher than in most sectors. A compromised portal doesn’t just expose order history — it disrupts the supply chain, delaying production schedules and risking plant operations. Buyer portals connect to ERP systems, CAD libraries, order histories, and sometimes even OT data from the floor. If a portal gets compromised, the damage doesn’t stop at stolen credit cards. It can expose production schedules, proprietary designs, and operational vulnerabilities. That’s the nightmare scenario every CISO is hired to prevent.
So when a supplier says, “Don’t worry, our IT team has it covered,” it doesn’t land. The buyer’s security team wants proof. They need to know the portal enforces multi-factor authentication, that order data isn’t stored in plain text, and that old plugins and apps aren’t ticking time bombs. If those answers aren’t clear and documented, the CISO will stall the deal, no matter how good the pricing is or how badly operations needs the part.
And this is where suppliers get blindsided. To sales, a portal is a sales tool, and to the buyer’s leadership, it’s a risk vector. If your e-commerce system isn’t hardened, you’re not just a vendor with a weak website, you’re a potential doorway into their network. No CISO in the world will put their name on approving that.
That’s why, for industrial suppliers, security has shifted from back-office IT work to a front-line sales issue. Passing a security audit isn’t “extra.” It’s the cost of entry. Without it, you won’t even get to compete.
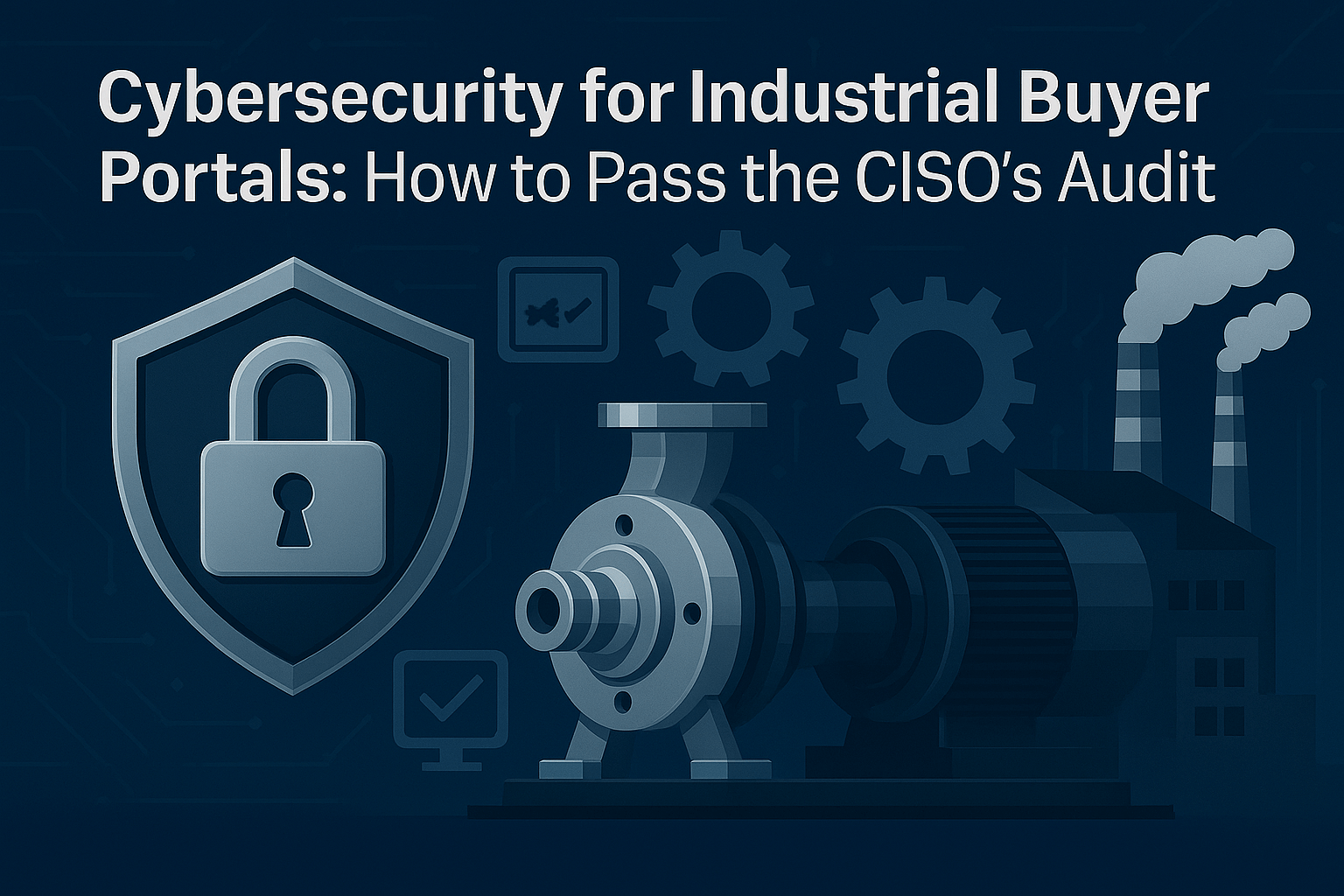
What CISOs Look For in an Industrial Supplier’s Portal
When a CISO looks at your portal, they’re not browsing features. They’re thinking about risk. Their job is to spot the weak link before it becomes tomorrow’s headline. The question running through their mind is simple: “If we open the door to this vendor, could they bring us down?”
That’s why their checklist is ruthless:
- Authentication. A password alone won’t cut it. If your portal doesn’t enforce multi-factor authentication (MFA) or support single sign-on (SSO), a stolen credential is all it takes to walk into sensitive order data. To a CISO, that’s unacceptable.
- Encryption. Quotes, CAD files, and invoices—they all carry sensitive data. If those files move without encryption in transit and at rest, it’s like shipping them in a clear envelope. Any breach along the way turns into a full-blown exposure.
- Access control. Not every buyer role should see the same thing. Procurement doesn’t need engineering specs. Junior staff don’t need contract pricing. A flat access model tells a CISO your governance is weak, and that’s a deal breaker.
- Data handling. Where is buyer data stored? For how long? Can dormant accounts be shut down cleanly? Order history and consumption patterns are intelligence gold and if you can’t explain how they’re controlled, a CISO won’t trust you with them.
- Monitoring and logging. If something suspicious happens — a login from another country, a flood of file downloads — can you see it? Too many portals operate like blind spots. Without logs and alerts, you can’t prove compliance, and you can’t contain a breach.
- Maintenance. Third-party apps are often the hidden hole. If your portal runs on outdated plugins, unpatched integrations, or untested code, the CISO doesn’t see useful functionality — they see an unlocked back door.
These aren’t academic questions. They’re the exact items that show up in vendor security questionnaires — the ones procurement officers slide across the table before they sign contracts. And if your answers are vague or thin, it doesn’t matter how competitive your pricing is. You won’t make it through the gate.
In today’s market, your portal isn’t just a storefront. To your buyer’s CISO, it’s part of their security perimeter. And no one in that role will compromise on protecting it.
Common Weak Points That Sink Supplier Portals
When supplier portals fail audits, it’s usually not because of some exotic, nation-state-style hack. It’s because of basic weaknesses — the kinds of things every CISO knows to look for and every vendor should have fixed.
Outdated apps and plugins.
Many industrial suppliers run their portals on Shopify Plus or BigCommerce with third-party apps layered on for quoting, file delivery, or account management. The problem? Those apps don’t always get patched. A forgotten update becomes an open door, and the buyer’s security team spots it immediately.
Exposed APIs.
Portals often connect to ERP or MRP systems through APIs. Without strong authentication — like tokenization or signed requests — those APIs can be exploited to siphon off order data or pricing intelligence. What looks like “just a connection” to sales is a red flag to a CISO.
CAD libraries with no guardrails.
Some suppliers try to be helpful by posting CAD files in open directories or unsecured cloud buckets. To engineering buyers, that feels convenient. To a security officer, it’s a nightmare: anyone with the link can access sensitive product geometry. In the wrong hands, that’s intellectual property theft.
Flat access across accounts.
Too many portals treat every buyer login the same. An intern with a guest account sees the same order history as the procurement director. That lack of role-based permissions makes CISOs nervous because it means sensitive data can spread too far inside the buyer’s organization and too easily outside it if the account is compromised.
No logging, no visibility.
This is one of the most damaging oversights. If the portal can’t show who accessed what, when, and from where, then during a breach you have no evidence to prove compliance or limit exposure. A CISO sees that gap and shuts the door on the deal.
In every one of these cases, the sales team thinks the portal is “good enough.” But the buyer’s security team sees an unlocked window, and no CISO signs off on a vendor with open windows.
The brutal truth is these weak points don’t just delay deals, they kill them outright. A buyer would rather go with a slower or more expensive supplier who passes security than risk signing with one who doesn’t.
Deployment Pattern: Secure Quoting + Order History
Two areas make CISOs lean in hardest during portal reviews: quoting and order history. Both contain the kind of information that, if exposed, damages not just the supplier but the buyer as well.
1- Quoting
Quoting isn’t just about pricing. It holds contract terms, discount structures, and margin-sensitive data. If a competitor ever got access to a buyer’s quote history, they’d know exactly how to undercut you. That’s why unsecured quoting flows are a deal killer.
Here’s how to secure them:
Never email quotes as open PDFs. Use tokenized, expiring links tied to the buyer’s account.
Encrypt quote documents at rest, not just in transit.
Log every access event: who viewed the quote, when, and from where. If procurement leadership asks, you should be able to prove a clear trail.
2- Order History
Order history is just as critical. To a CISO, it’s not just a log of past purchases — it’s a map of a buyer’s consumption patterns. How often they reorder, which plants use which parts, what volumes move at what time of year. If that leaks, it’s a blueprint for operational vulnerability.
Here’s how to protect it:
Restrict order history visibility by account role. Procurement leads need the data; not every engineer does.
Rate-limit and monitor access to prevent scraping or bulk export by compromised accounts.
Encrypt order history at rest and apply the same logging rules as quotes. Every view or download should be traceable.
When you lock down quoting and order history this way, you send a message to buyers: we understand what’s sensitive, and we protect it like you would. That’s exactly what a CISO needs to hear before they sign off.
Because in industrial commerce, protecting a buyer’s order history is protecting their competitive advantage. And if your portal can’t do that, you won’t be trusted with their business.
The Audit Lens: Questions CISOs Will Ask Suppliers
When a buyer’s CISO runs an audit, it doesn’t feel like a casual chat. It feels like an interrogation. They don’t want marketing promises; they want evidence of a documented security process and hard answers to back it up. If your team can’t provide them, the deal slows, stalls, or dies.
Here are the kinds of questions that routinely show up in vendor security reviews:
- Authentication:
“How do you handle user logins? Do you enforce multi-factor authentication? Do you support SSO?” - Testing and patching:
“When was the last penetration test on your portal? Who ran it? Can you provide the report?” - Data storage:
“Where is buyer data stored? Which region? Which provider? How is it encrypted at rest?” - Access control:
“Can you restrict what different roles can see inside the portal? Who decides that mapping?” - Incident response:
“What’s your documented plan if a breach occurs? How quickly are customers notified? Who owns remediation?” - Third-party risk:
“Which apps and services are connected to your portal? How do you verify they’re patched and safe?” - Compliance:
“Do you align with frameworks like NIST, SOC2, ISO 27001? Can you provide proof?”
Every one of these questions has to be answered in writing, often before procurement will move the deal forward. And “we’re working on it” isn’t an answer.
The companies that win are the ones that develop this preparation into a repeatable part of their sales cycle. They rehearse the answers, document the controls, and build a playbook their reps can hand to buyers without scrambling.
Because when the audit comes, speed and clarity are what close the gap between “pending” and “approved.”
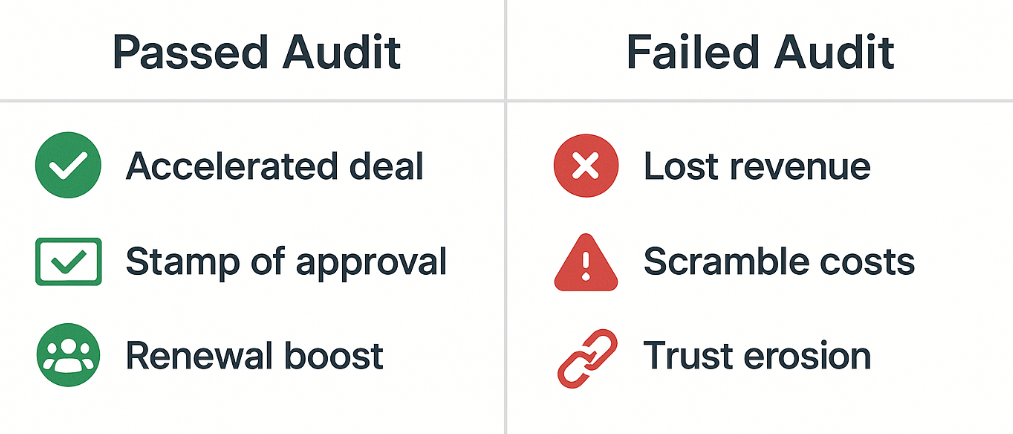
The Business Impact of Passing (or Failing) the Audit
Security reviews don’t just tick boxes. They decide whether revenue flows or stops cold.
When you pass the audit, deals move faster. Procurement doesn’t stall the contract in legal review. CISOs don’t need weeks of back-and-forth. The confidence is there, and the order flows. More importantly, you become the supplier procurement can defend inside their own organization: “Yes, they passed our security review. They’re safe to work with.” That stamp of approval shortens sales cycles and strengthens renewals.
When you fail the audit, the damage cuts deeper than the delay. Deals don’t just pause — they die. The buyer may quietly blacklist you for future bids, marking you as “too risky.” Even if you patch the issues later, the reputational hit lingers. A CISO who red-flagged your portal once won’t forget. And your competitors will be only too happy to remind the buyer that their portal passed without hesitation.
The costs add up fast:
- Lost revenue. A stalled seven-figure contract that never closes.
- Scramble costs. Emergency patches, last-minute consultants, and re-architecting under pressure.
- Trust erosion. Procurement teams hesitate to rely on your portal, defaulting to phone and email instead — undoing the very ecommerce efficiency you built.
The truth is in today’s industrial sales, passing a CISO’s audit is as critical as competitive pricing or product quality. A missing control is no different from a missing capability, it keeps you out of the deal.
That’s why forward-looking suppliers don’t wait for the audit to find problems. They run the same checks internally, fix gaps before buyers ask, and show up ready with answers. In a world where every contract renewal comes with a security review, that preparation isn’t optional. It’s survival.
Future-Proofing Security in Industrial Commerce
The mistake most suppliers make is treating security as a project, something you scramble to fix when a buyer pushes back, then set aside until the next fire. That cycle is what keeps portals vulnerable and sales teams exposed.
The reality is that cyber threats evolve faster than procurement cycles. What passed last year’s review may fail this year’s. A plugin patched six months ago may already have a new vulnerability. Hackers don’t wait for your budget cycle, and neither do buyers’ security teams.
Future-proofing means treating security as part of operations, not as an emergency. That starts with rhythm:
- Routine code scans and penetration testing. Not once a year, but on a regular cadence. Every new deployment, every app update, and every integration gets tested.
- Governance over third-party apps. Each add-on you bolt onto Shopify Plus or BigCommerce is another doorway. Without oversight, those doors stay unlocked.
- Separation of OT and IT. In industrial commerce, your buyer portal should never touch plant-floor systems. Keeping operational technology isolated isn’t just best practice — it’s a line in the sand buyers demand.
- Documented playbooks. Not just for incident response, but for answering audits. A living record of policies, patches, and procedures turns what could be a scramble into a confident checklist you hand to the buyer’s security team.
Suppliers who build this discipline don’t just avoid breaches. They gain an edge. Because when a buyer’s CISO sees that your portal isn’t just patched but governed, logged, and monitored, they stop viewing you as a risk and start viewing you as the safe choice.
And in industrial B2B, “safe” is the reputation that wins contracts long after pricing stops being the deciding factor.
Passing the CISO’s Portal Audit
Security Readiness Checklist
Think of this like a pre-flight inspection before you let revenue take off. Every box unchecked is a place where a buyer’s CISO will press — and possibly block the deal.
| Area | What to Check | Why It Matters | Status |
| Authentication | MFA on all purchasing accounts; SSO enabled | CISOs reject password-only logins | ☐ / ☐ |
| Encryption | TLS 1.2+ for data in transit; AES-256 at rest | Protects quotes, CAD files, and order data | ☐ / ☐ |
| Role-Based Access | Map permissions by job role, not convenience | Prevents interns seeing pricing or CAD IP | ☐ / ☐ |
| Data Lifecycle | Define retention rules, purge stale accounts | Hoarded data = uncontrolled risk | ☐ / ☐ |
| Logging & Monitoring | Track every login, download, anomaly | Proves compliance, speeds incident response | ☐ / ☐ |
| Maintenance | Scan code and apps regularly; patch & document | Outdated plugins are the #1 CISO red flag | ☐ / ☐ |
| System Segregation | Keep ecommerce isolated from OT networks | Prevents ecommerce from being an attack bridge | ☐ / ☐ |
Controls to Implement (Do Now / 30 Days / 90 Days)
How to use: Treat this like a build plan. The acceptance criteria are what a CISO will want to see.
| Window | Control | Acceptance Criteria |
| Now (0–2 weeks) | Enforce MFA, enable SSO for enterprise accounts | MFA enforced on purchasing roles; SSO via SAML/OIDC. Provide admin evidence + test login video. |
| Now | Inventory all Shopify/BigCommerce apps + ERP/MES/CPQ integrations | Risk register completed with last-patch dates, data scope, and vendor accountability. |
| Now | Verify TLS 1.2+ and HSTS; confirm platform encryption at rest (AES-256) | External scan report + platform security documentation. For custom services, screenshots of encryption settings. |
| 30 days | Centralize logs (auth, file access, exports) + configure alerts | Log samples + alert rules (failed logins, scraping attempts, anomalous downloads). |
| 30 days | Tokenized quotes; expiring links (no static PDF attachments) | Sample tokenized quote + link expiry policy. |
| 30 days | Rate-limit and secure APIs for order history + ERP integrations | WAF/rate-limit config, OAuth2/HMAC token auth, and test results. |
| 30 days | Role definitions + least-privilege access matrix | Role matrix doc + quarterly review cadence with audit log samples. |
| 90 days | Penetration test + app code scan (with remediation plan) | Pentest report (redacted) + list of closed findings. |
| 90 days | OT/IT segregation review & diagram | Updated network diagram + attestation from IT/OT owners. |
| 90 days | Incident Response runbook + tabletop exercise | Runbook link + tabletop notes + on-call contact tree. |
Third-Party Risk Register (Apps & Integrations)
How to use: This is your buyer’s favorite page. Keep it current and you’ll defuse half the audit.
| App/Service | Purpose | Perm Scope / Data Touched | Last Patch | Risk (H/M/L) | Mitigation | Decision |
| Quoting App X | Quotes | Prices, discounts, contracts | 2025-07-12 | M | Tokenized links, no email PDFs | Keep |
| File Delivery Y | CAD downloads | CAD (STEP/IGES), user IDs | 2025-08-02 | H | Login required, expiring links, watermark | Keep w/ controls |
| ERP Connector Z | Pricing/Inventory | SKUs, price lists, order lines | 2025-06-28 | M | Signed tokens, allow-list IPs | Keep |
| Analytics W | Usage metrics | Pageviews, IPs | 2025-03-10 | H | Remove (no value vs. risk) | Remove |
Secure Quoting & Order History Pattern
How to use: CISOs lean in here. Score yourself and fix gaps before they ask.
Quoting Controls Scorecard (Pass/Fail)
Quotes delivered via tokenized, expiring links (no static PDFs) → ☐ Pass ☐ Fail
Quotes encrypted at rest; access logged (who/when/IP) → ☐ Pass ☐ Fail
Role-based access (only authorized buyer roles view quotes) → ☐ Pass ☐ Fail
No quotes exposed via public URLs or email attachments → ☐ Pass ☐ Fail
Order History Controls Scorecard (Pass/Fail)
Encrypted at rest; role-scoped visibility → ☐ Pass ☐ Fail
Rate-limits + anti-scraping/WAF enabled → ☐ Pass ☐ Fail
Export guardrails (approval, throttling, audit log) → ☐ Pass ☐ Fail
Retention policy defined (and enforced) → ☐ Pass ☐ Fail
Audit Q&A Crib Sheet (Answers You Can Prove)
How to use: Assign owners, link evidence. Reps can attach this to vendor questionnaires.
| CISO Question | Your Answer (Short) | Owner | Evidence |
| Do you enforce MFA/offer SSO? | Yes. MFA enforced on purchasing roles; SSO via SAML/OIDC. | Policy + test | |
| How is data encrypted? | TLS 1.2+ in transit; AES-256 at rest (storefront, files, DB). | Screenshots + certs | |
| How do you control access? | Role-based access; least-privilege; quarterly audits. | Role matrix + review log | |
| How are quotes delivered? | Tokenized, expiring links; no email attachments; full access logs. | Flow diagram + logs | |
| Can you prevent scraping of order history? | Yes. WAF + rate limits + behavioral alerts. | WAF config + alert rules | |
| Last penetration test? | 2025-Q2 by third party; critical/high closed; report available under NDA. | Redacted report | |
| Where is data stored? | <Region/Provider>; CAD in secured bucket with expiring links. | Architecture + policy | |
| Incident response? | 24h notification SLA; named on-call; tabletop completed Q3. | Runbook + tabletop notes | |
| Third-party governance? | Risk register; patch cadence tracked; removal policy enforced. | Risk register |
Revenue Impact Dashboard (Security as Sales Enablement)
How to use: Track monthly. If these move the right way, your security is helping sales.
| Metric | Baseline | Target |
| Vendor security questionnaire cycle time | 21 days | ≤ 7 days |
| Deals stalled by security review | 6/quarter | ≤ 1/quarter |
| High-severity findings (open) | 5 | 0 |
| App patch SLA (days to patch) | 21 | ≤ 7 |
| MTTD / MTTR (security events) | 5d / 9d | ≤ 1d / ≤ 3d |
| Quote/email exposure incidents | 4/quarter | 0 |
| % enterprise accounts using SSO | 10% | ≥ 60% |
Final Note
CISOs don’t expect perfection. They expect control, proof, and a plan. If your team can produce this toolkit on request, security stops being a blocker and starts being the reason the deal closes.
Security as a Revenue Strategy
Deals don’t fall apart because your catalog is weak or your pricing is off. More often, they die in silence because a buyer’s CISO flagged your portal as unsafe. That’s the reality of industrial commerce today: security isn’t a back-office IT matter anymore. It’s the first gate every contract has to pass through.
The suppliers who understand this shift don’t just patch holes when audits show up. They treat security like a sales strategy. They walk into negotiations knowing their portal can withstand scrutiny, that every question has an answer, and that nothing about their systems will stall the deal. Buyers notice. CISOs notice. And once you’ve proven yourself safe, procurement stops hesitating and starts trusting.
The ones who don’t? They’ll keep getting blindsided. Deals will vanish. Accounts will quietly slip away. And no amount of apologizing will fix a reputation once a buyer marks you as “too risky.”
If your portal hasn’t been tested the way a buyer’s CISO will test it, you’re gambling with contracts. The safe move is to run the audit yourself first.
Contact us, we’ll tell you exactly where your portal passes, where it fails, and how to fix it before the buyer ever sees the gaps. Because in this market, security isn’t just about keeping data safe. It’s about keeping revenue alive.